This is the write-up for the Nostalgia Cryptography Challenge from CyHub 2023's Hac-Man CTF event. The organizers designed it to be exceptionally challenging, necessitating familiarity with various common encodings, encryption methods, and hashing algorithms.
Nostalgia
INFO
Below is the Nostalgia challenge's solution from the CyHub 2023 CTF (Hac-Man) that occurred on November 17-18, 2023.
Description:
You remember Ms. PacMan, but do you remember me?...
My dear space cadetYou remember Ms. PacMan, but do you remember me?...
My dear space cadetAttached File:
Solution
We started by unzipping the ZIP file attached to the challenge, and this is what we found.
pinball
│ FONT.DAT
│ PINBALL.DAT
│ pinball.exe
│ PINBALL.MID
│ PINBALL2.MID
│ SOUND1.WAV
│ SOUND104.WAV
│ SOUND105.WAV
│ SOUND108.WAV
│ ...
│ SOUND735.WAV
│ SOUND8.WAV
│ SOUND827.WAV
│ SOUND9.WAV
│ SOUND999.WAV
│ table.bmp
│ wavemix.infpinball
│ FONT.DAT
│ PINBALL.DAT
│ pinball.exe
│ PINBALL.MID
│ PINBALL2.MID
│ SOUND1.WAV
│ SOUND104.WAV
│ SOUND105.WAV
│ SOUND108.WAV
│ ...
│ SOUND735.WAV
│ SOUND8.WAV
│ SOUND827.WAV
│ SOUND9.WAV
│ SOUND999.WAV
│ table.bmp
│ wavemix.infInteresting! This seems like the very popular and old game Pinball, and there is an executable file pinball.exe which we can use to launch the game.
Note
The CTF challange was completely solved on a Windows machine, but if you were on UNIX/GNU Linux during the CTF there's a way to run this executable using Wine.
And that's what we did, we executed the file and it thankfully launched the actual game.
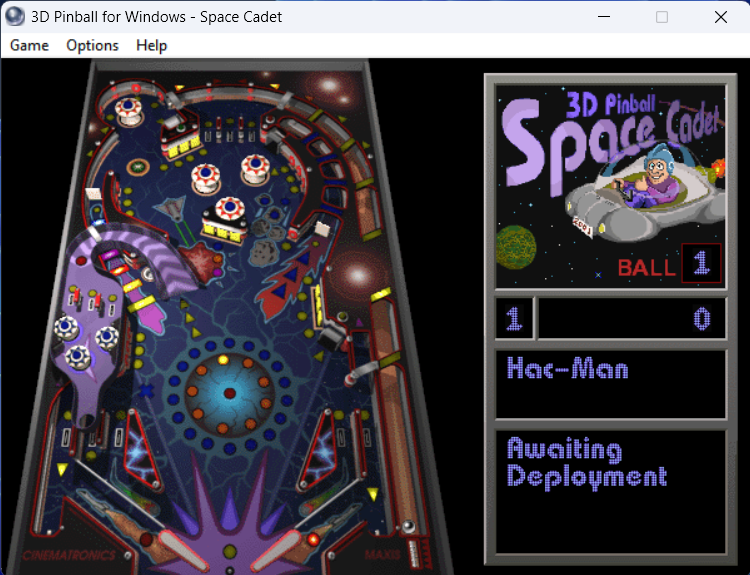
Hmm... I don't recall seeing anything related to "Hac-Man" in this game, did I?
Well, it appeared to be a altered version of the game, so we decided to play it and check if there were any modifications to the game mechanics. That's when something else unusual occurred.
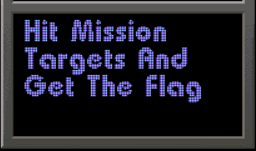
I observed that hitting the mission targets is necessary to obtain the flag. Intrigued, I decided to play around a bit to understand the situation better. During my exploration, I noticed some peculiar texts on the panel—some resembling hashes and others less obvious. I documented all my findings with screenshots. Here's a summary of what I discovered:
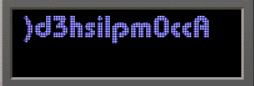
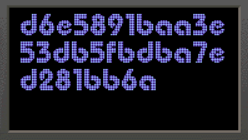
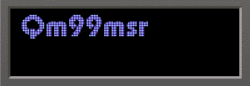
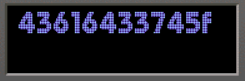
Having engaged in numerous cryptography challenges, I recognized that these components form part of the actual flag. However, due to my reluctance to manually record them, I opted for an alternative approach. Essentially, I tried to find the source of these strings and successfully located it by extracting the contents of the pinball.exe file.
Inside the executable file, there existed a file named string.txt containing various strings utilized in the game. I uncovered the peculiar-looking strings displayed in the game, and I've highlighted the relevant portions below:
...
5 } d 3 h s i l p m 0 c c A
6 h a c m a n {
...
4 4 4 3 6 1 6 4 3 3 7 4 5 f
...
4 9 Q m 9 9 m s r _
...
1 0 6 d 6 e 5 8 9 1 b a a 3 e 5 3 d b 5 f b d b a 7 e d 2 8 1 b b 6 a
......
5 } d 3 h s i l p m 0 c c A
6 h a c m a n {
...
4 4 4 3 6 1 6 4 3 3 7 4 5 f
...
4 9 Q m 9 9 m s r _
...
1 0 6 d 6 e 5 8 9 1 b a a 3 e 5 3 d b 5 f b d b a 7 e d 2 8 1 b b 6 a
...After removing the extra whitespaces, I obtained the following result:
1. }d3hsilpm0ccA
2. hacman{
3. 43616433745f
4. Qm99msr_
5. d6e5891baa3e53db5fbdba7ed281bb6a1. }d3hsilpm0ccA
2. hacman{
3. 43616433745f
4. Qm99msr_
5. d6e5891baa3e53db5fbdba7ed281bb6aThe 2nd string appeared to be the initial segment of the flag.
While the 1st one initially appeared to be the ending segment of the flag, it wasn't completing the actual form of a CTF flag, because flags end with }, so I reversed the string using a very famous cryptography tool called CyberChef and got the ending segment of the flag!
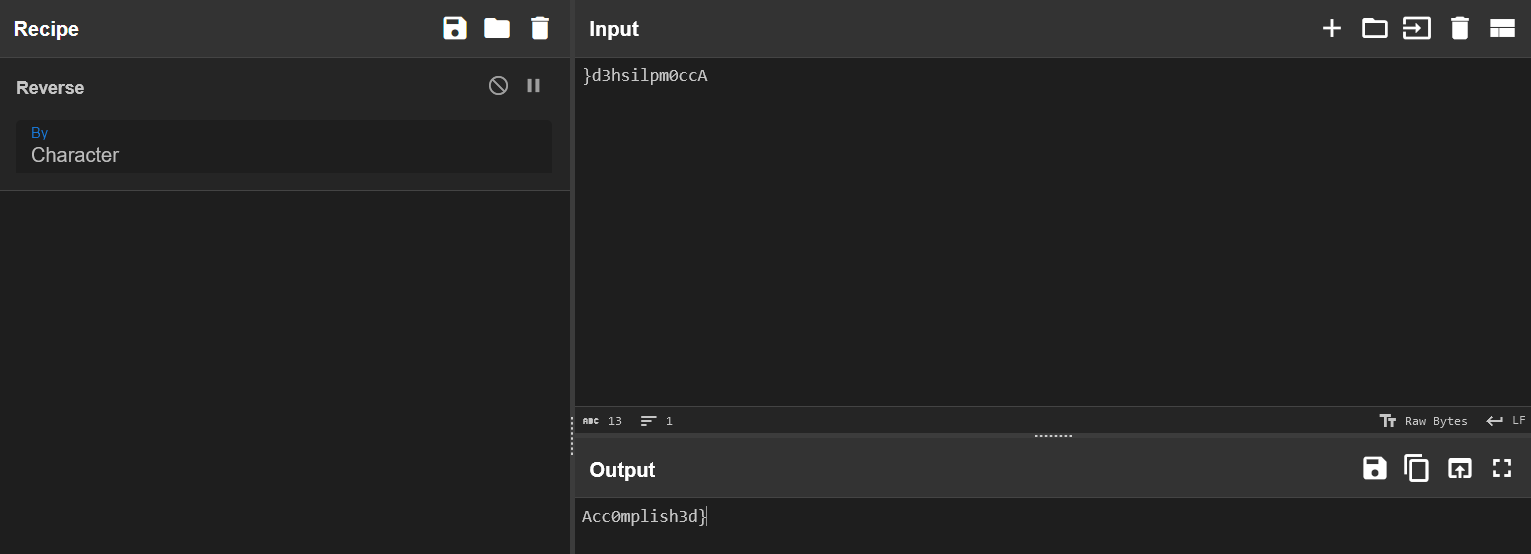
Acc0mplish3d}Acc0mplish3d}Yep! word Accomplished leet encoded.
So at this point we have the first and last segment of the flag, and we have to figure out what the others are.
hacman{ ... Acc0mplish3d}hacman{ ... Acc0mplish3d}Continuing, I observed that the 3rd and 5th discoveries consisted entirely of hexadecimal characters, leading me to thinking that these were hash values, so I went to Google and tried to find some online hash crackers to hash those.
I tried very famous online hash crackers but they failed to crack, and then after digging a little bit, I found Hashes.com which cracked both of the hash digests. Here are the results of what the cracked hases looked like.
43616433745f:Cad3t_
d6e5891baa3e53db5fbdba7ed281bb6a:Sp4ce_43616433745f:Cad3t_
d6e5891baa3e53db5fbdba7ed281bb6a:Sp4ce_After this, I tried to form the flag, and submitted.
hacman{Cad3t_Sp4ce_Acc0mplish3d}hacman{Cad3t_Sp4ce_Acc0mplish3d}But, it was incorrect so the remeaining piece Qm99msr_ had to probably take place in the flag.
The last piece didn't make any sense but I tried to play around a little bit by using Dcode.fr Cesar cipher brute-forcer and discovered some interesting things.
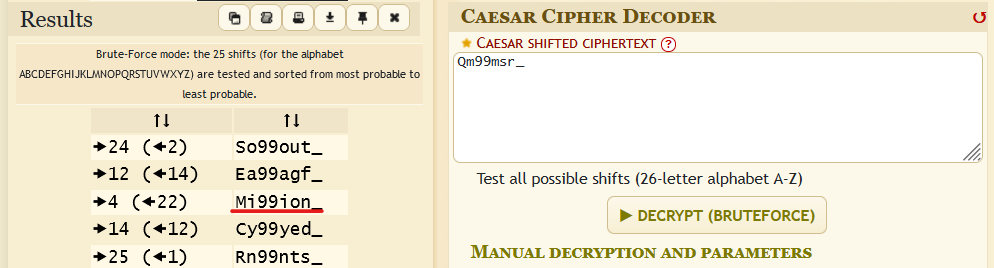
The one highlited one (shifted 22 times) seemed to be the leet encoded word of Mission, and so I formed the flag again and submitted!
hacman{Cad3t_Sp4ce_Mi99ion_Acc0mplish3d}hacman{Cad3t_Sp4ce_Mi99ion_Acc0mplish3d}And it failed again, at this point I was stuck. I was staring at the current formed flag, and then I realized that there is seem to be an issue, so I tried something.
S is 5 in leet encoding, then why is it 9 in the mission's S letters instead of 5? Maybe there had been something wrong while encoding? Maybe?
So, I replaced the Mi99ion with Mi55ion, and formed the new flag.
hacman{Cad3t_Sp4ce_Mi55ion_Acc0mplish3d}hacman{Cad3t_Sp4ce_Mi55ion_Acc0mplish3d}Andddd it was correct!! 🎉🎉
Note
I don't exactly remember the actual order of these words that formed the flag, so this might not match the real correct flag in the CTF. If you remember the actual one, please hit me up on Discord and I will fix it.
Conclusion
Solving the game challenge required understanding codes. It was interesting and needed careful exploration. I am glad that I was able to construct the correct flag after ~2 hours of figuring it out and seeking for some hints.
 Mher's Blog
Mher's Blog